
Avas Secure E-mail Gateway
Filters and controls both inbound and outbound e-mail traffic of the corporate e-mail server,protecting from malicious attacks such as Malware, Phishing, Spearphishing, outbreaks and domain and brand abuses xx.

Filters and controls both inbound and outbound e-mail traffic of the corporate e-mail server,protecting from malicious attacks such as Malware, Phishing, Spearphishing, outbreaks and domain and brand abuses xx.

AVAS SEG flters e-mails departing your corporate e-mail server, thus protecting your brand and network reputation. Making sure DMARC and proper DLP (Data Loss Prevention) are configured, it's very unlikely your brand gets abused, and very likely your legitimate e-mails reach the inboxes of receivers. It applies potent antivirus and antispam based on Machine Learning
AVAS SEG is implemented in a private cloud of dedicated, related containers with dedicated IP addresses.That way, your company is automatically protected from 'noisy neighbors',and made sure that other companies' blacklisting, backscattering and outbreaks will not affect your network reputation and operation.
Besides the usual white and blacklist of e-mail addresses, domains and IP addresses, AVAS SEG has an extensive set of options to tweak in order to adjust to your company's sending and receiving profile.
AVAS SEG secures your e-mail with a concentric ring of tunable firewalls. The outermost ring is a strict firewall of real-time IP addresses that are performing attacks detected by the community and our Threat Intelligence, and filtered accordingly.
AVAS SEG utilizes opensource code, as it is publicly audited for increased security, and Machine Learning algorithms to predict malicious attacking IPs and user behaviour. It makes extensive use of encryption and TLS options to ensure encrypted mail transport channels. Planisys combines a mix of Virus Signatures from its own Threat Intelligence and third parties
Unwanted e-mail with spam-like patterns is being flagged at different thresholds, to make sure the least dangerous or dubious are detected as such by the corporate e-mail server, and the most spamming ones directly get discarded.
In order to early block Ransomware attacks, AVAS SEG gets a feed of virus block lists with more than 35.000 DGA (domain generated algorithm) domains and 500,000 RBL/RPZ domains, as well as malicious IP addresses detected at Planisys infrastructure in Europe, USA and Latin America.
PDNS is Planisys own DNS infrastructure and Web-UI , to implement DNS to announce domain sending policies as well as SSL certificates and roots of trust with technologies such as DNSSEC and resource records like CAA, SPF, DMARC, DANE, DKIM and CAA.
AVAS SEG allows you to separate outgoing traffic through SBR (Sender Based Routing), that is, relays dedicated to certain senders. In this way, you can assign a different treatment to certain senders to isolate them from more polluted channels, such as those originated in internal alert application mails.
AVAS SEG integrates with Active Directory, so your company can benefit from avoiding Dictionary attacks, Bounce amplification, and to avoid outbreaks by internal equipment that has been infected with some sort of malware.
Avascloud SEG differentiates multiple types of attacks, and has different options to combat any of them. This is the case for DDoS, Ransomware, Phishing, malware in general, Spearphishing, other viruses and spam.
DMARC is an authentication protocol to block spoofing and so protect your brand from impersonation and abuse. With Planisys' PDNS, we configure DMARC properly in order to announce to third parties including you , that when an email sender is in your domain, only SPF- and DKIM-validated emails should be accepted.

To protect against spear-phishing also known as BEC (Business Email Compromise), which is the most feared form of deception in the financial and human resources departments of corporations, and considering that these messages target specific individuals, a comprehensive E-mail Security Monitoring, such as the one offered by Planisys AVAS SEG, is needed. By combining several techniques involving DNS, PKI and ML, spear-phishing attacks can be reduced to marginal percentages.

AVAS Secure E-Mail Gateway filters and controls e-mails exiting your corporate e-mail System before they enter the Internet. It recognizes outbreaks, it filters outbound viruses and malware, protecting the reputation of your domain and brand in the Internet.

Spear-phishing also known as BEC (Business Email Compromise), is the most feared form of deception in the financial and human resources departments of corporations. A comprehensive e-mail Security Monitoring is needed in order to thwart the social engineering staged by the attackers
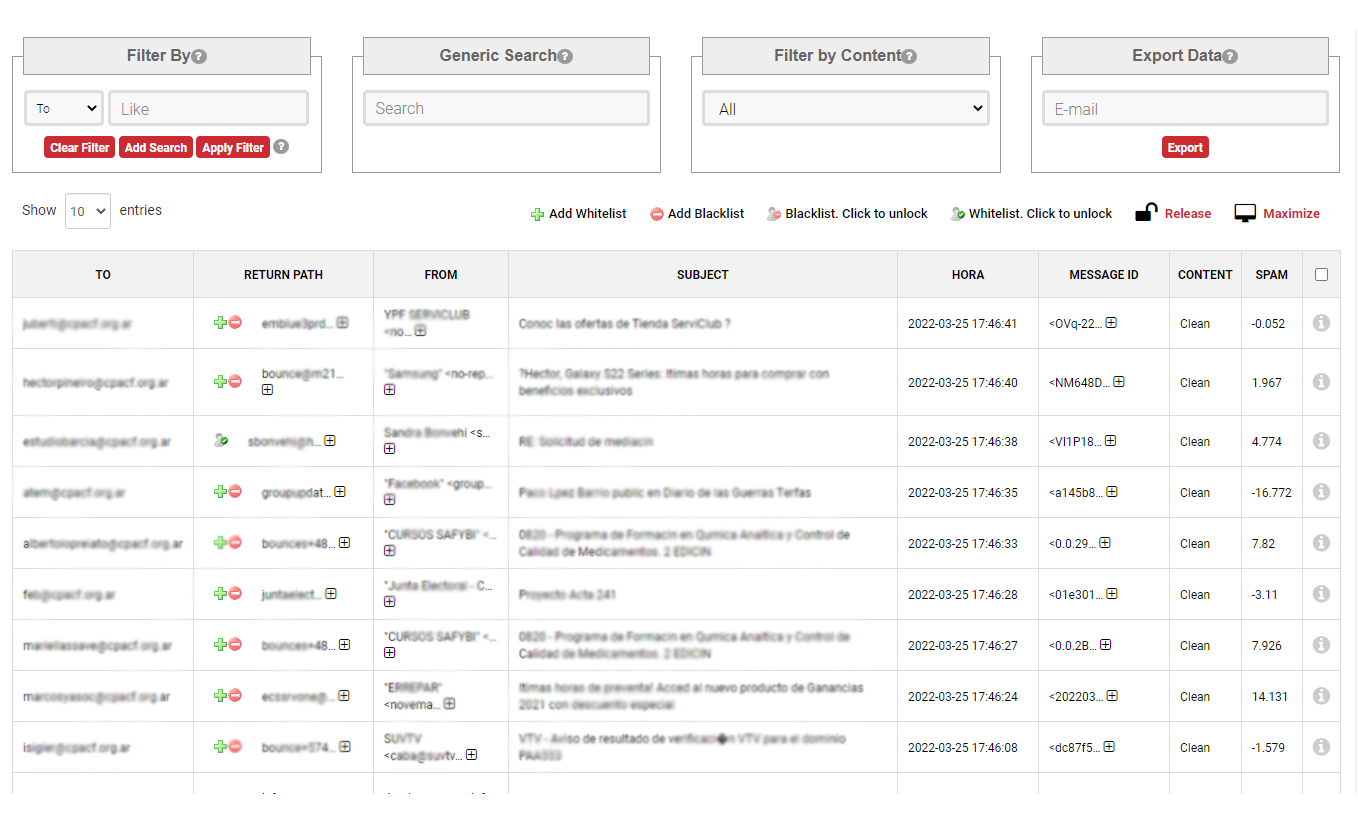
Mailaudit is an extremely useful web interface for both admins and users, that lets them browse the log of headers of received and sent e-mails, filter them by quarantine, spam, virus and clean, order and search, as well as configure quarantine alerts and release.
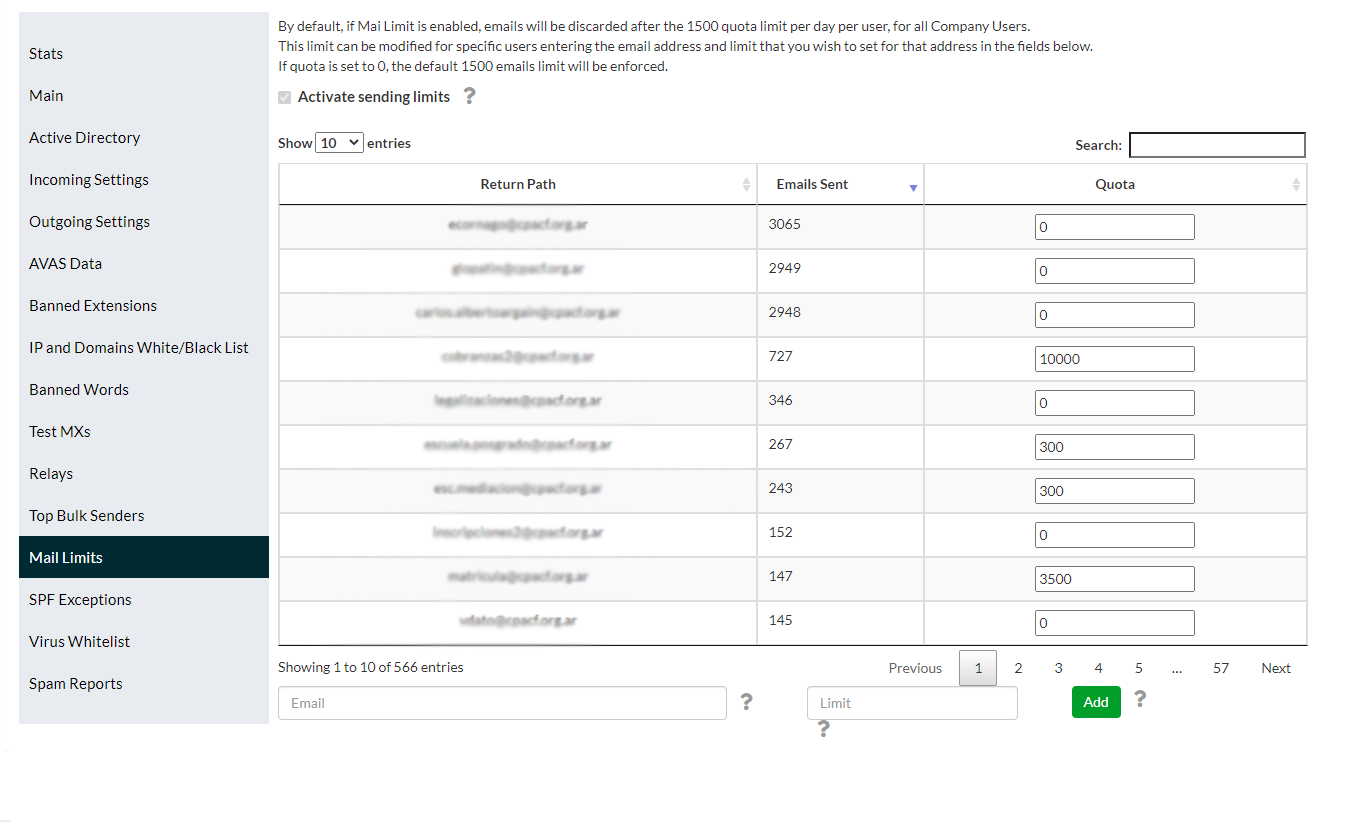
Maillimit is a setting that permits visualization of a sender ranking, plus imposing limits in real-time when Outbreaks or Workstation/equipment infection are being detected, so that e-mails above the limit can be silently discarded.
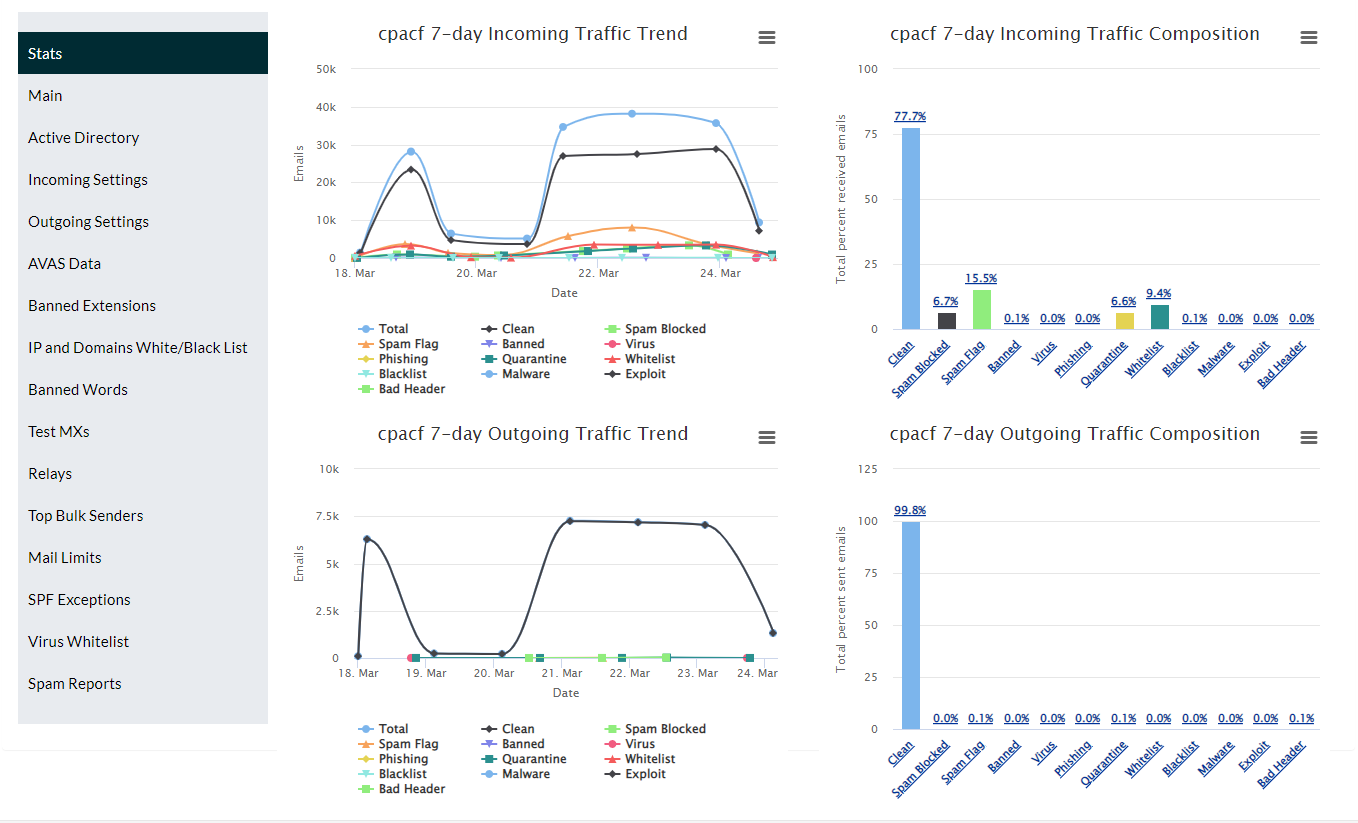
With the inbound e-mail statistics, you can visualize in curves and histograms the relative quantities of received e-mail, classified and segmented according to spam level, virus infection, malware detection and white/blacklisting.
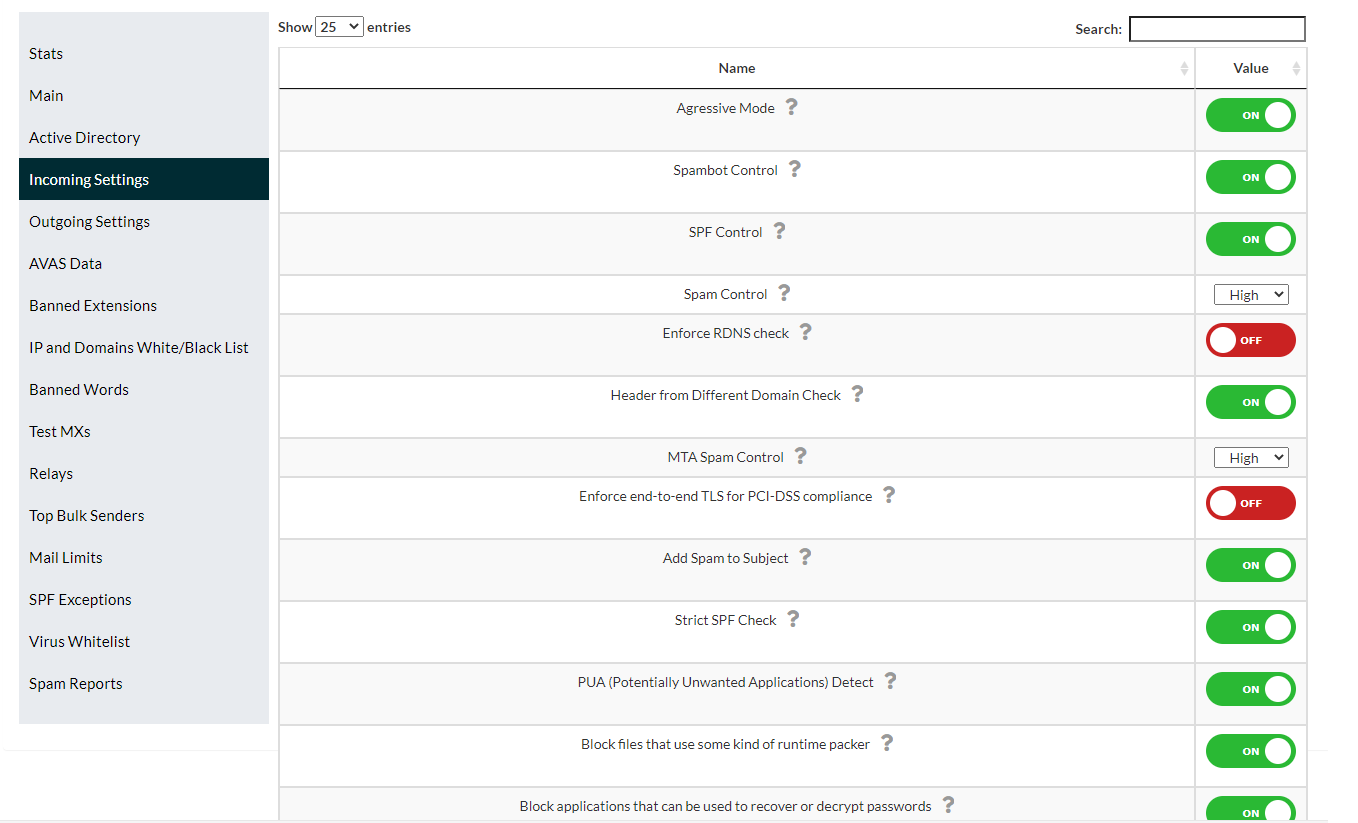
The incoming configuration allows to establish parameters for each client, adjusting their tolerance to spam, mass e-mail and anomalies of other domains.
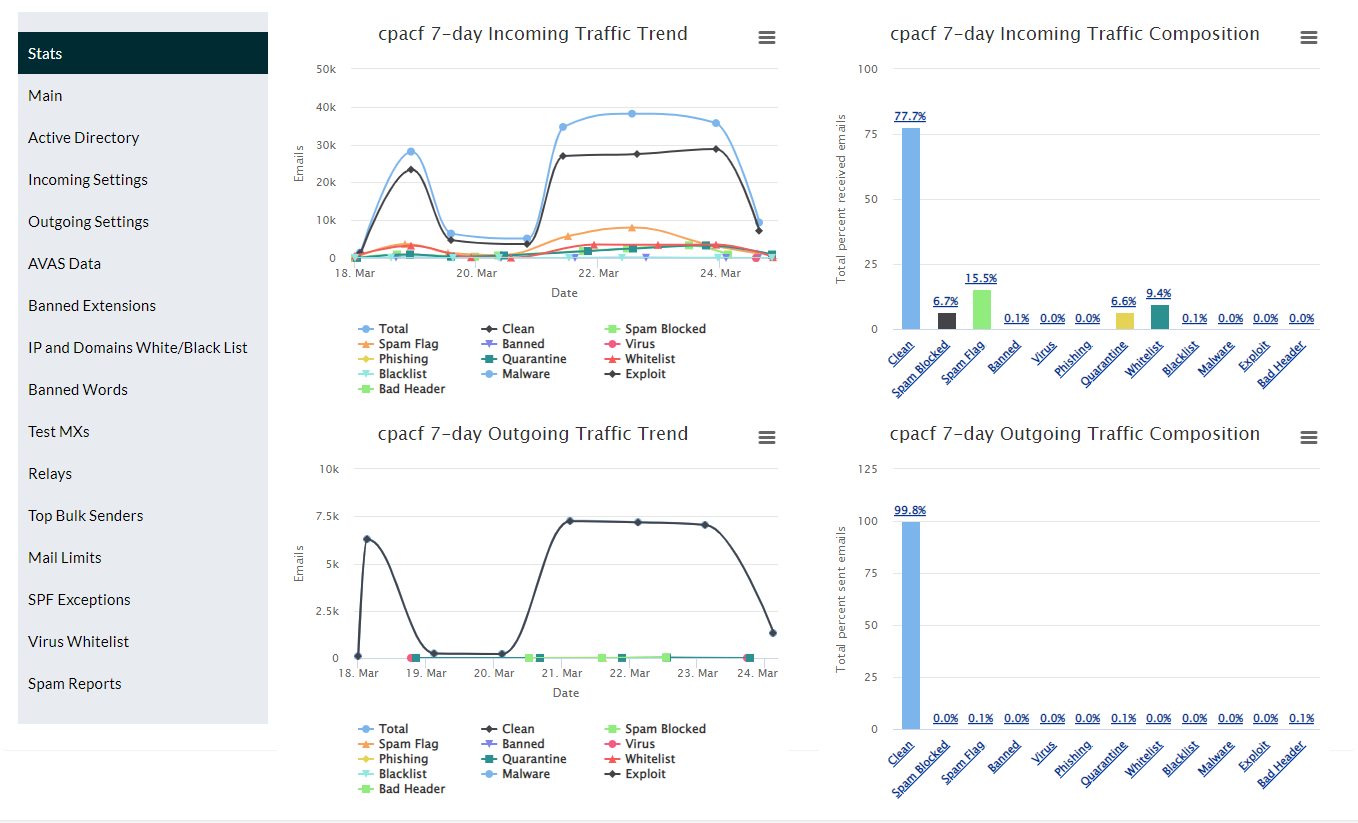
The incoming configuration allows to establish parameters for each client, adjusting their tolerance to spam, mass e-mail and anomalies of other domains.