Attack mitigation by Planisys DNS Firewall


The ClearFake malware, that invites the end user to update Chrome or Edge browser, can be easily mitigated with Planisys RPZ (Response Policy Zones), as part of the Planisys DNS Firewall.
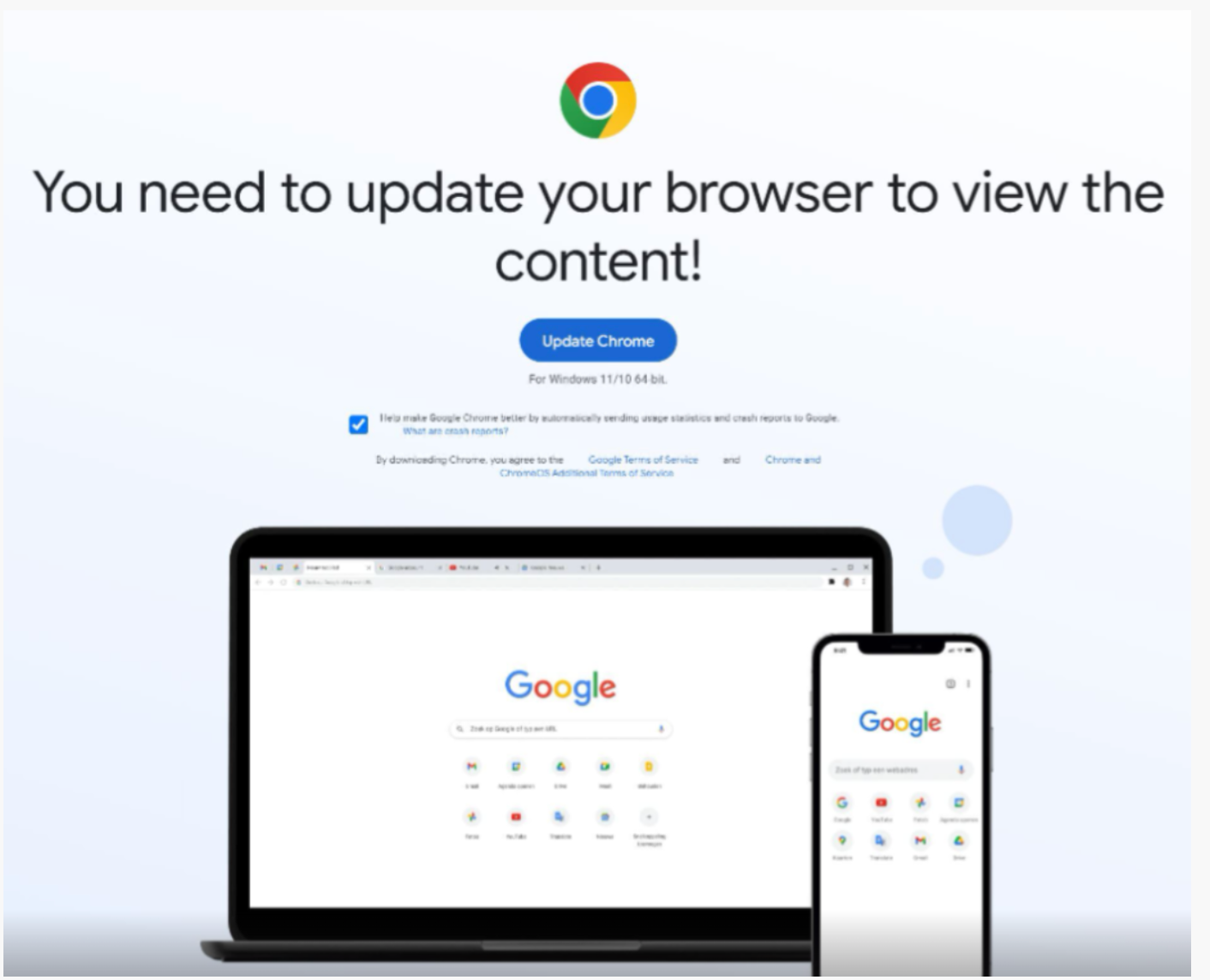
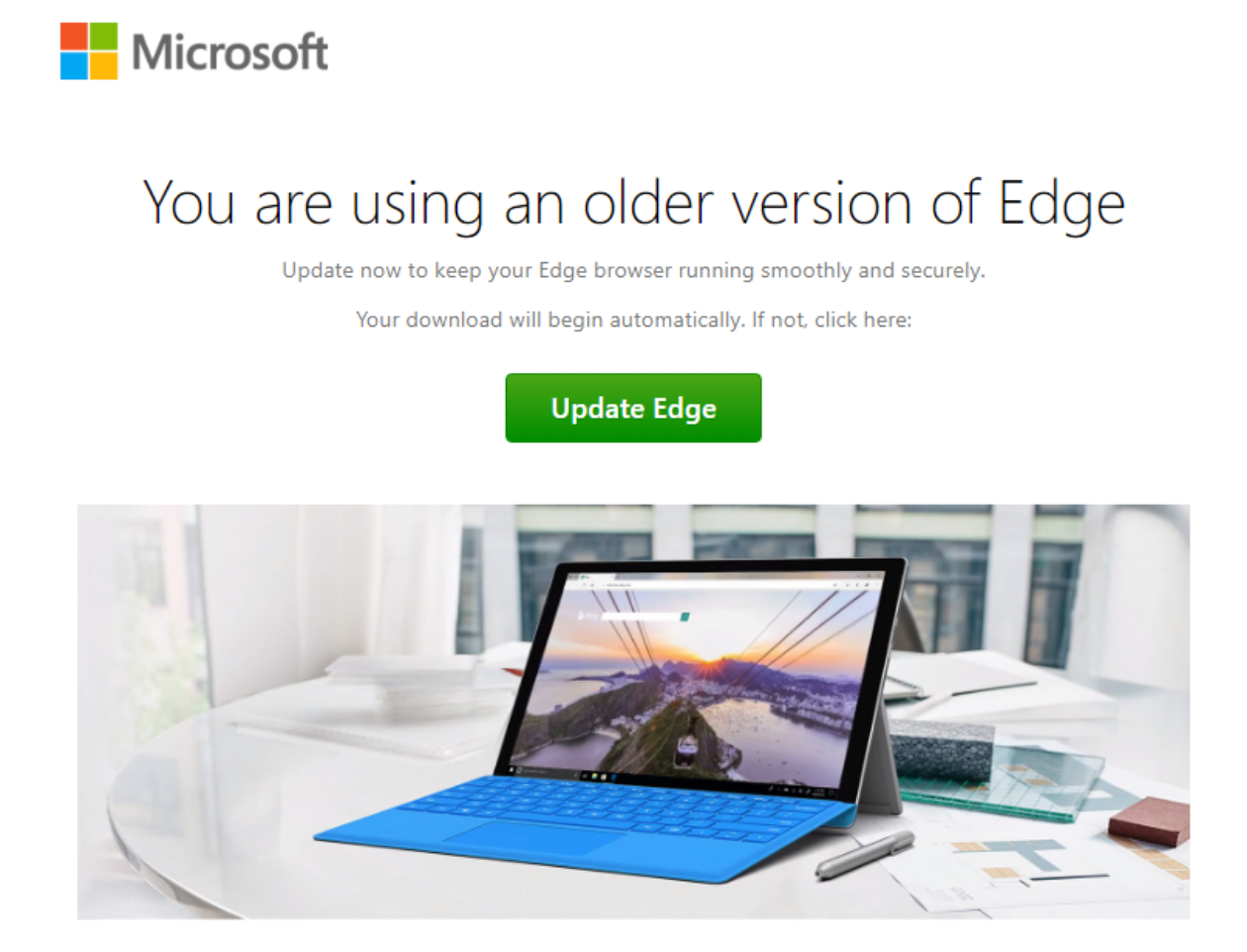
If the users resolve domain names through a regular resolver, they are most likely going be trapped and infected, at least with a downloader.
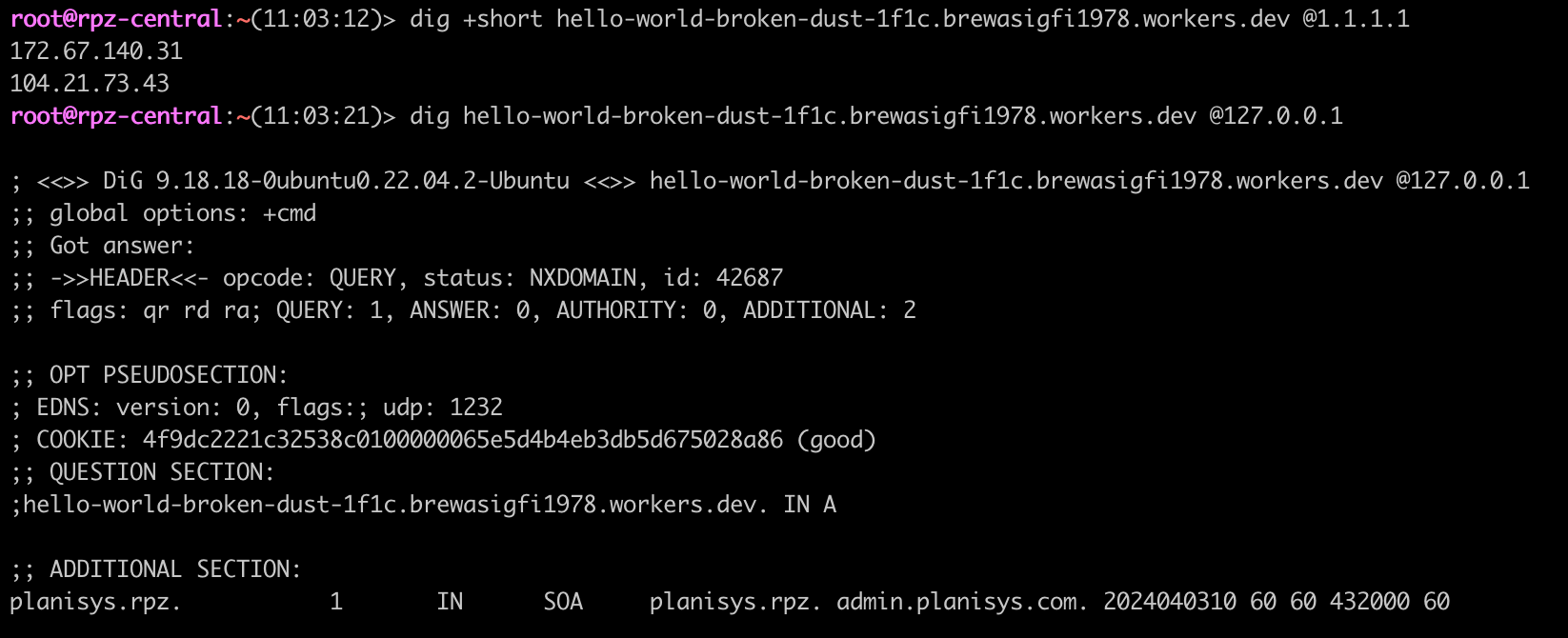
The domains involved are being resolved by public resolvers like e.g. Cloudflare's 1.1.1.1 , but not by Planisys RPZ if you use it as your resolver.
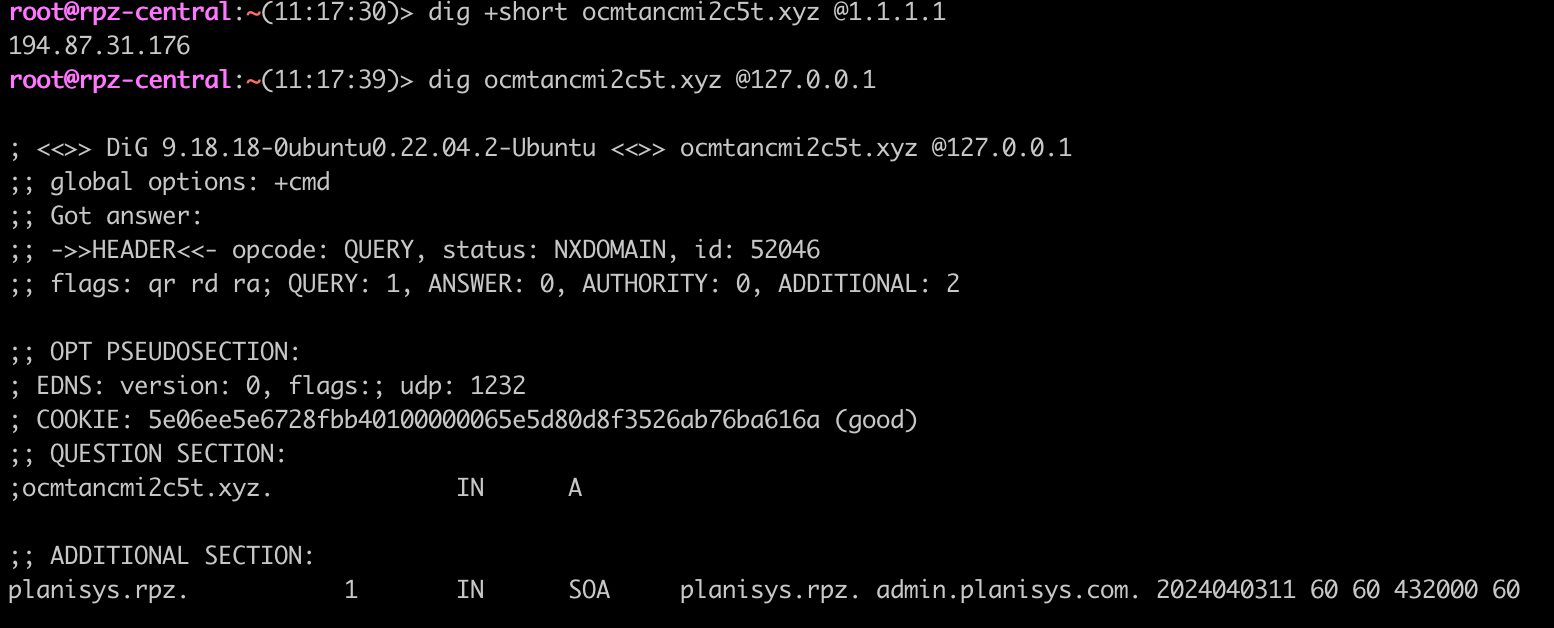
When the users' browsers try to resolve the involved domain names, Planisys RPZ will return NXDOMAIN thus avoiding the trap.
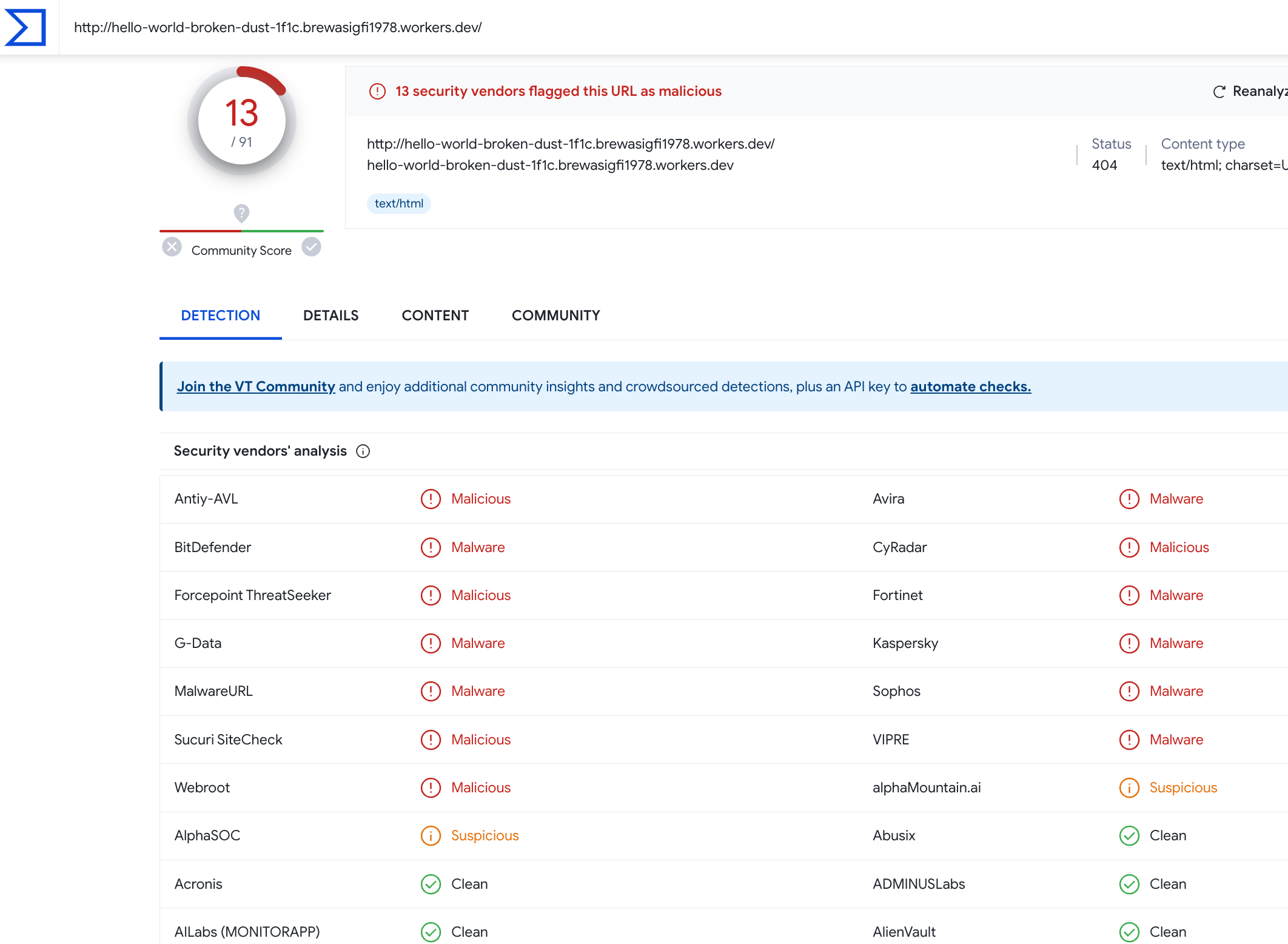
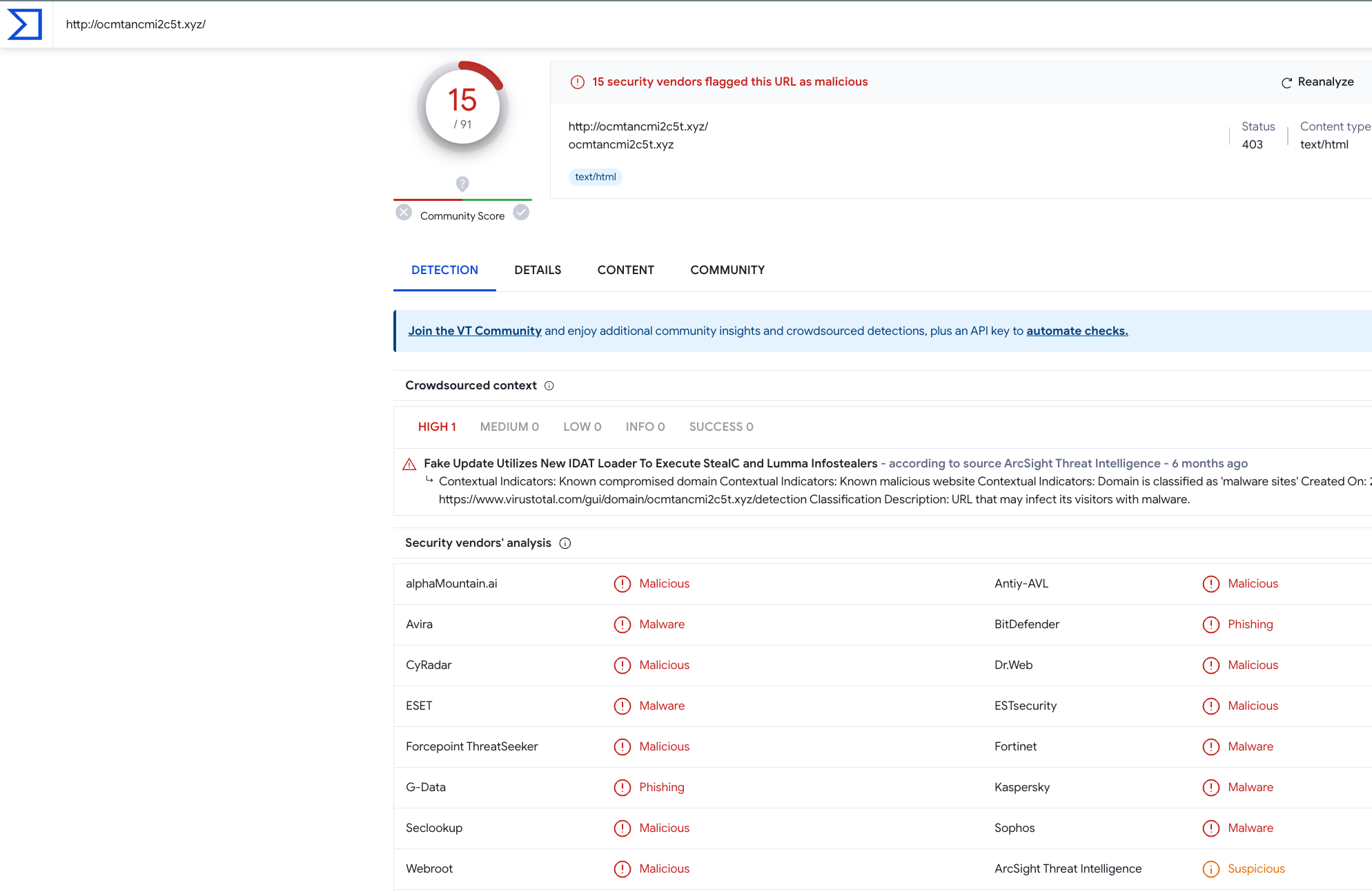
Here are more domains involved in this attack, as detected by VirusTotal:
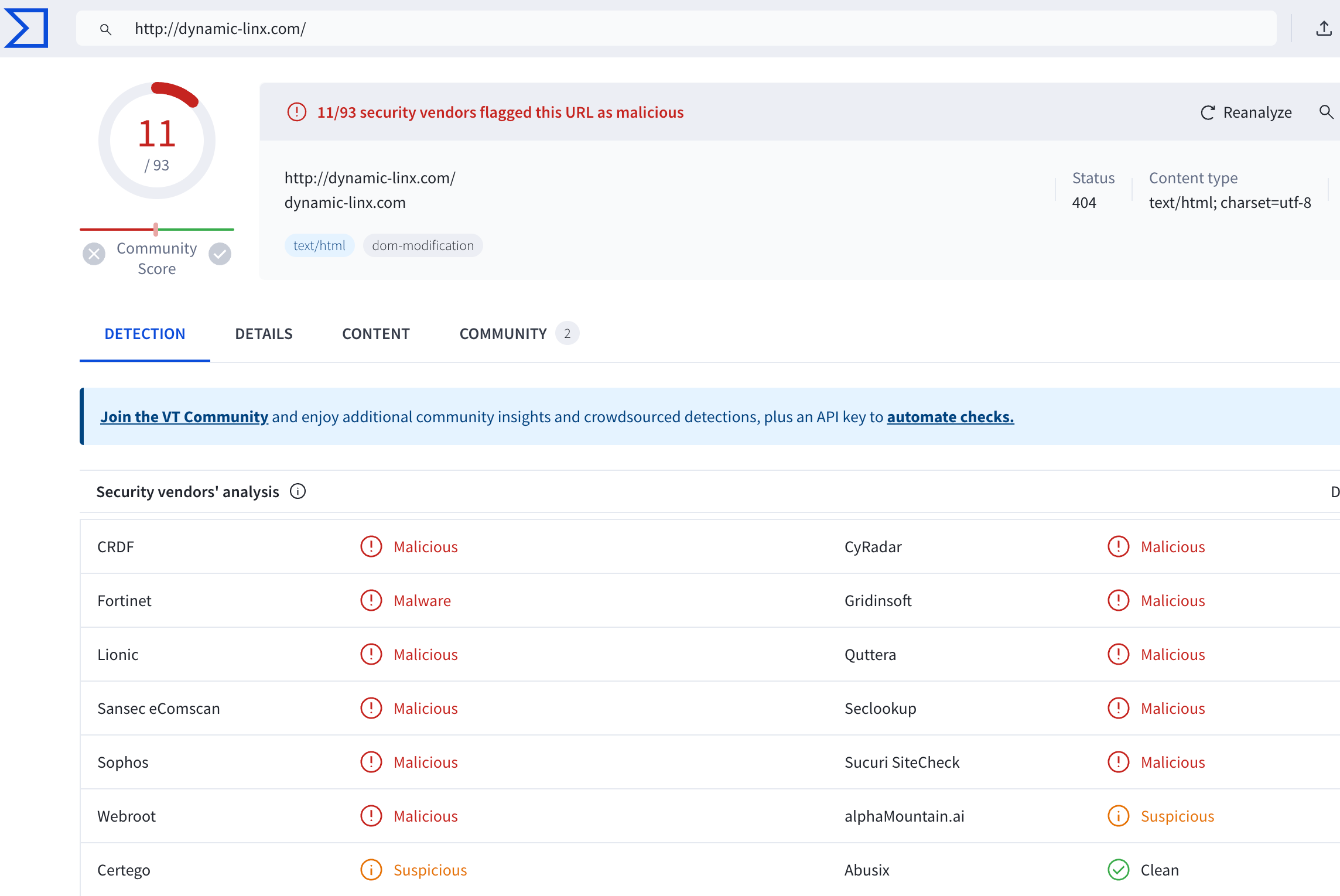
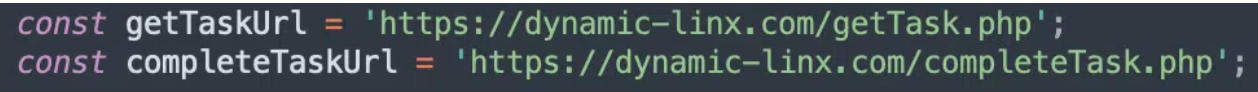
Please bear in mind that attackers can quickly change the domains where they host their malware, so both Wordpress admin and xmlrpc.php should only be granted access to trusted IPs, which you can perform putting Planisys CDN in front of your Wordpress website.