The KEYTRAP Attack
The recently discovered KeyTrap attack in February 2024 is one of the most dangerous Denial-of-Service (DoS) threats to date. A single malicious packet can overload a resolver’s CPU, rendering an entire DNS infrastructure unresponsive.
The CVSS (Common Vulnerability Scoring System) severity rating for this vulnerability is 7.5 out of 10, highlighting its critical nature.
Fortunately, Debian 12 has promptly addressed this issue with security patches.
Planisys has proactively updated all its DNS servers to the latest version, ensuring our DNSaaS customers remain protected.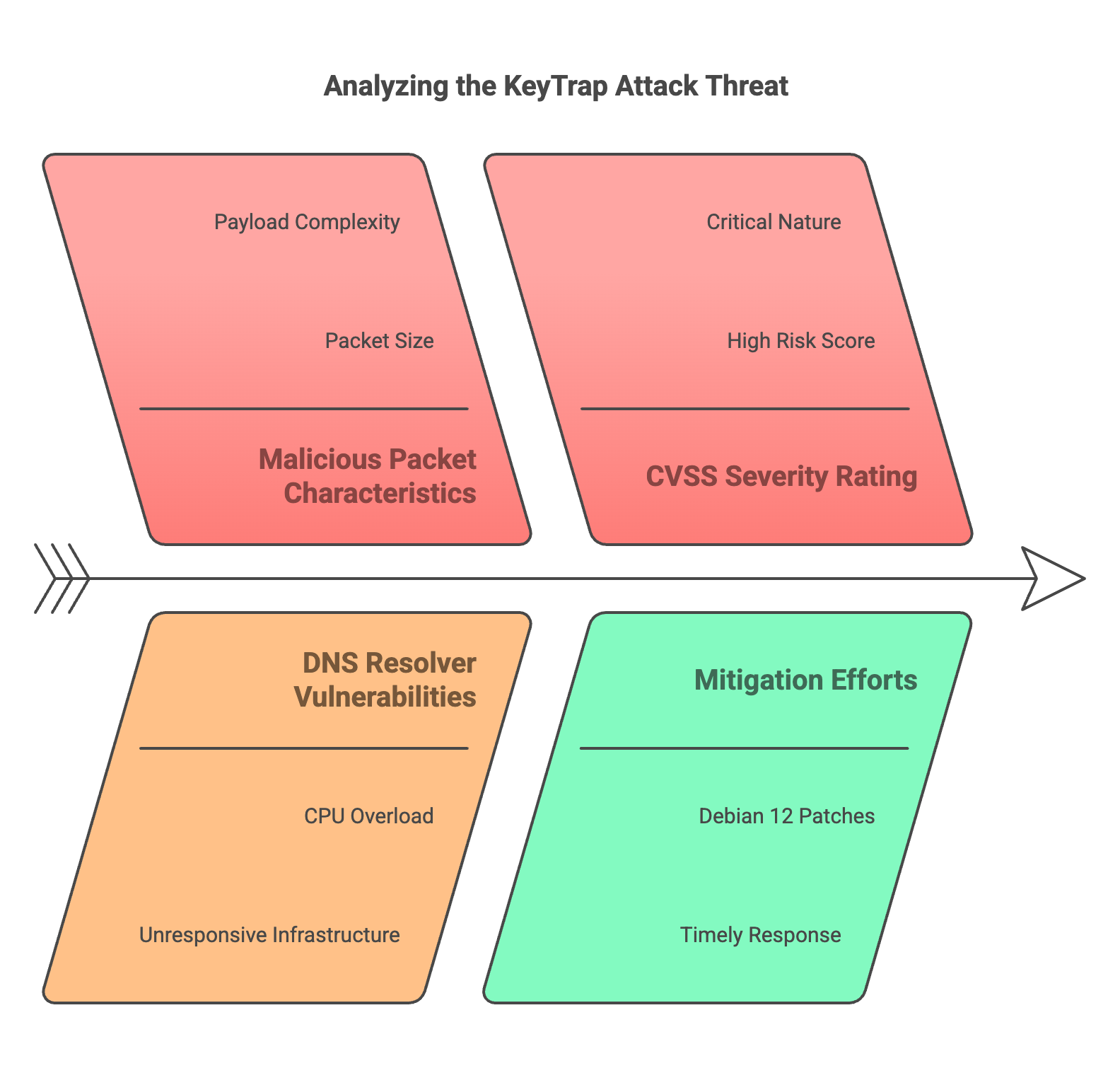
NXDOMAIN Attack Variants
NXDOMAIN is a negative response indicating that a domain does not exist. Attackers exploit this by flooding a resolver with non-existent domain queries, leading to a Random NXDOMAIN attack. When the attack targets authoritative DNS servers with non-existent subdomains, it is known as a Phantom Subdomain NXDOMAIN attack.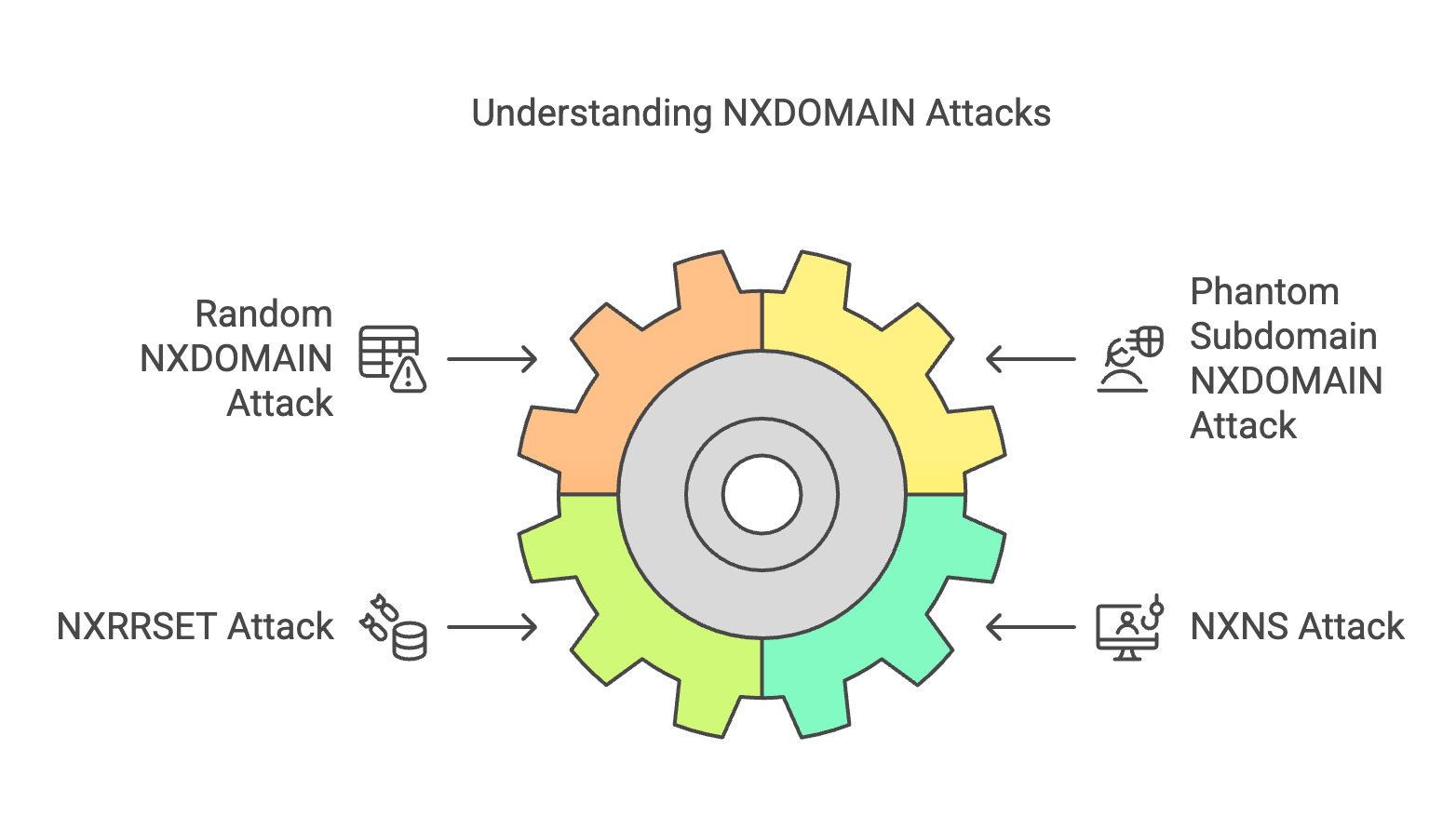
These attacks are commonly launched by botnets, leveraging thousands of compromised devices, making them difficult to mitigate. The impact includes CPU exhaustion, cache pollution, and degraded query response times.
Additional NXDOMAIN-based threats include:
- NXRRSET attack: Overloading the server with queries for non-existent resource records, such as AAAA (IPv6) queries.
- NXNSAttack: Leveraging fake subdomains and non-existent glue records to exhaust resolver and upstream authoritative resources.
In all cases, these attacks aim to disrupt the DNS hierarchy by overloading recursive resolvers and upstream authoritative servers.NXDOMAIN Attack Mitigation by Planisys DNS Firewall
Planisys DNS Firewall employs multiple strategies to counteract NXDOMAIN-based attacks:
- DNSSEC Enforcement: Utilizing NSEC records for immediate and efficient negative caching, reducing unnecessary query loads. This method, known as Aggressive Use of DNSSEC-Validated Cache (RFC 8198), significantly improves performance.
- Machine Learning-based Anomaly Detection: A trained Random Forest model detects botnet query patterns in real-time, blocking malicious traffic dynamically.
- Real-time Log Analysis: Monitoring excessive NXDOMAIN responses to adjust cache expiration dynamically and optimize recursive timeout settings.
- Controlled Rate-Limiting: Ensuring fair resource allocation while whitelisting trusted networks to avoid false positives.

DDoS Attack Variants
A Distributed Denial-of-Service (DDoS) attack can overwhelm a DNS server, either by flooding it with excessive queries (DNS Floods) or exploiting misconfigured servers for amplification attacks.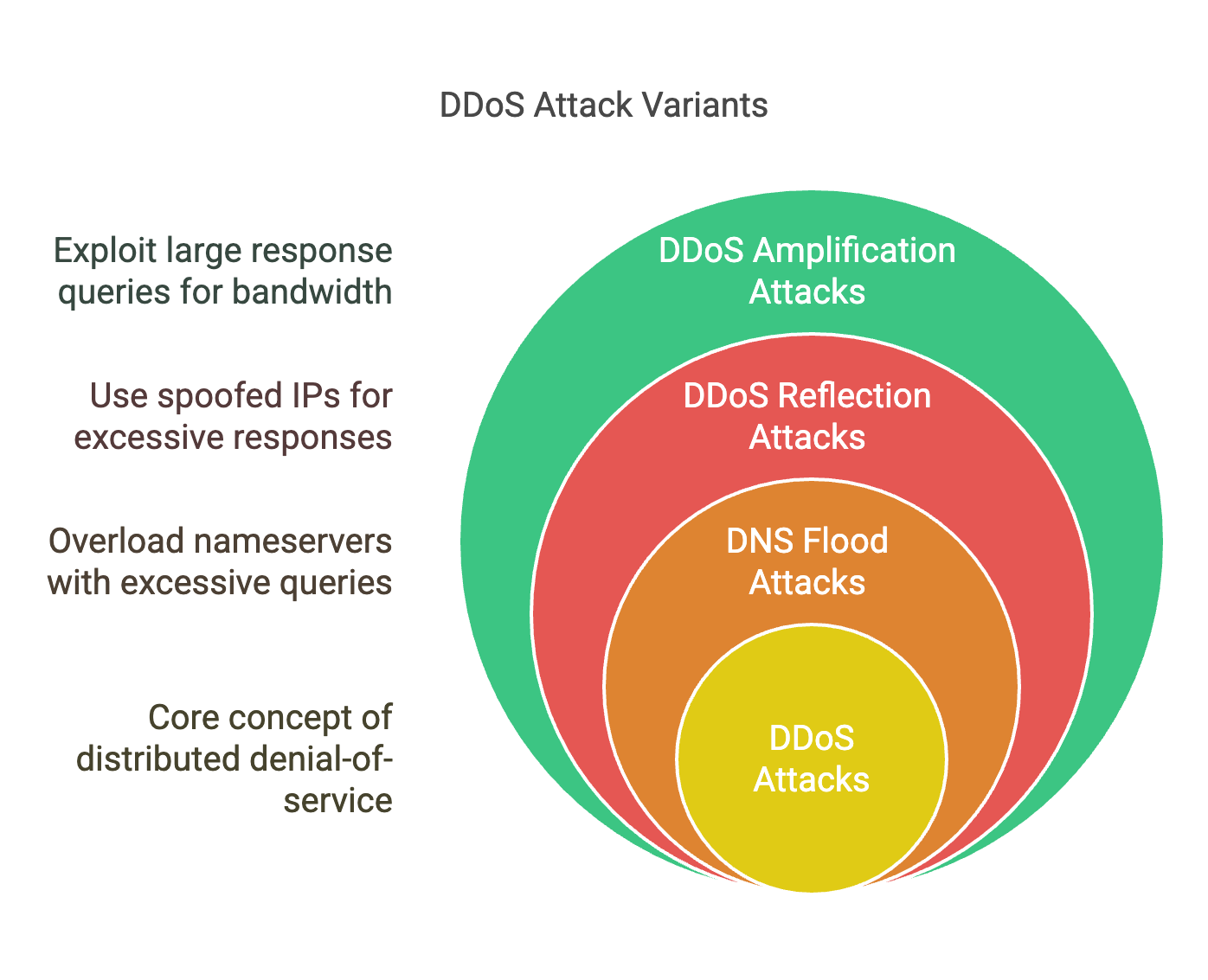
- DNS Flood Attacks: These attacks overload a nameserver with valid but excessive queries, consuming its resources.
- DDoS Reflection Attacks: Attackers use spoofed IP addresses to flood victims with DNS responses, effectively using the nameserver as an unwitting amplifier.
- DDoS Amplification Attacks: Exploiting DNS queries that return disproportionately large responses, such as ANY or DNSSEC requests, maximizing bandwidth consumption.
DDoS Attack Mitigation by Planisys DNS Firewall
To counteract DDoS attacks, Planisys DNS Firewall implements:
- Rate-Limiting: Filtering and restricting excessive queries while allowing trusted traffic.
- Forced TCP Fall-back: Flagging excessive UDP queries to force TCP-based resolution, slowing down the attacker naturally.
- ML-Based Traffic Analysis: Detecting patterns matching known attack datasets, triggering automated defenses.
- Geographically Distributed DNS Servers: Utilizing multiple high-capacity links to withstand large-scale attacks.

DNS Tunneling
DNS tunneling is a technique used for data exfiltration and command-and-control (C&C) communication through DNS queries. Malware-infected devices can use DNS TXT records to send stolen data or receive attack payloads.
- Malware-based C&C Communication: The infected device queries specially crafted domains to receive commands.
- Data Exfiltration: Attackers encode stolen information into DNS queries, bypassing traditional network monitoring.
DNS Tunneling Mitigation
- RPZ Filtering: Blocking known tunneling domains using a constantly updated Response Policy Zone (RPZ) database.
- Pattern Recognition: Detecting unusually long domain names and excessive TXT queries as potential exfiltration attempts.
- ML-Based Detection: Leveraging AI-trained models to flag and block suspicious traffic patterns.